Vulnerability Management
In the modern business landscape, vulnerability management is not just a checkbox, it’s a foundational element of Corporate Risk Management and Governance
Vulnerability Management: A Vital Cybersecurity Cornerstone
Vulnerability Management
Vulnerability management is the systematic process of identifying, assessing, prioritizing, and mitigating security vulnerabilities to protect against potential exploitation and maintain a secure digital environment.
Web Application Security
Web application security within vulnerability management entails safeguarding online applications from potential threats and vulnerabilities through proactive identification, mitigation, and continuous monitoring.
Policy Compliance
Policy Compliance refers to the adherence to established rules, regulations, and standards within an organization, ensuring that operations, processes, and behaviors align with predefined policies and guidelines.
Remediation
Remediation is the process of addressing and resolving identified vulnerabilities or issues to improve the security posture and functionality of a system, network, or application.
.

Integrated Vulnerability Management
The solution that offers the most extensive and all-encompassing approach to vulnerability management exercises, catering to organizations with diverse operational capacities, emerges as the optimal choice for contemporary digital enterprises. Vulnerability management involves identifying, assessing, addressing, and reporting on security vulnerabilities present in systems and the software operating on them. When integrated with other security measures, it becomes crucial for organizations to prioritize potential threats and reduce their exposure to attacks.
Features of Integrated VM
Remediation / Optimization Settings
Risk Meter
Autoassign / Bulk Assignation
Predefined Notifications
SLA Configuration
Integrations Available







Our highly anticipated product offering seamlessly incorporates a comprehensive vulnerability management component that encompasses and unifies capabilities from nearly all prominent vulnerability management solutions available in the market.
Working Process of our Solution
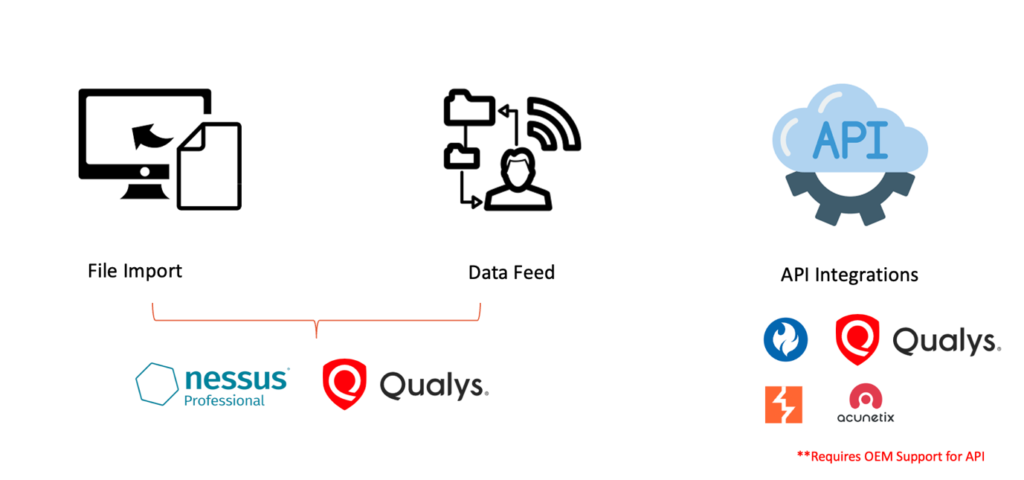
Unlocking Security: A deep dive into our Vulnerability Management solution's operational Process
The solution is highly adaptable and can interface with virtually any intricate vulnerability management system, such as Qualys, Acunetix, Burp Suite, HCL AppScan, and other OEM solutions that provide API access. The solution supports three distinct integration modes. The platform facilitates both one-way and two-way integration, offering the flexibility to initiate the entire process from Compliance Foresight and manage it within the solution itself. This streamlined approach eliminates the need to log into multiple tools and fetch reports separately, thereby enhancing efficiency.
Overall Process of the System

Navigating the full spectrum: The comprehensive process of Vulnerability Management
VM process helps the organizations to initiate the scans and manage all data across the infrastructures in a single platform with all scanning process happening at the backend. Once the API’s are integrated, users will just need to manage the scans and all related data across the infrastructures through the common unified platform. It is critical for organization to know the patching status through automated means and not only rely on users to inform the patching pointers. Compliance Foresight – VM Module has a very unique feature where it compares the last two scans to suggest if the patching is done. This helps the infrastructure team to verify the patching.
KEY BENIFITS TO ORGANIZATION
CISO Dashboard , Department Dashboards
Reduced Overhead in managing Organization Vulnerability
Single Solution to manage all organization vulnerabilities
Real Time Dashboards
Reduced Complexities
Pre–Defined Reports in excel and PDF
Trend Analysis of the vulnerabilities across servers, applications and devices
Business Level Ownerships and Vulnerabilities Closure
Automatic Patching Compliance
Tracker for Vulnerability Assessment, Policy Compliance and Web Applications
Mechanisms to raise exceptions and Exceptions Dashboards
Track all exceptions and reports and trends on defined period
Contact Info
- 1309 Coffeen Avenue STE 1200 Sheridan, WY 82801 United States
- sales@whitehats.tech
- ( +1 ) 307 257 6763
Open Hours
9:30AM – 05:30PM
