Vulnerability Management

Integrated Vulnerability Management-
The most comprehensive with overall 360 degree of the Vulnerability Management exercise across the organization with operational capability makes it the best fit solution for modern age digital organizations.
Vulnerability management is the process of identifying, evaluating, treating, and reporting on security vulnerabilities in systems and the software that runs on them. This, implemented alongside with other security tactics, is vital for organizations to prioritize possible threats and minimizing their “attack surface.”


Integrated Vulnerability Management
Our most awaited solution integrated Vulnerability Management that integrated almost all leading Vulnerability Management solutions.
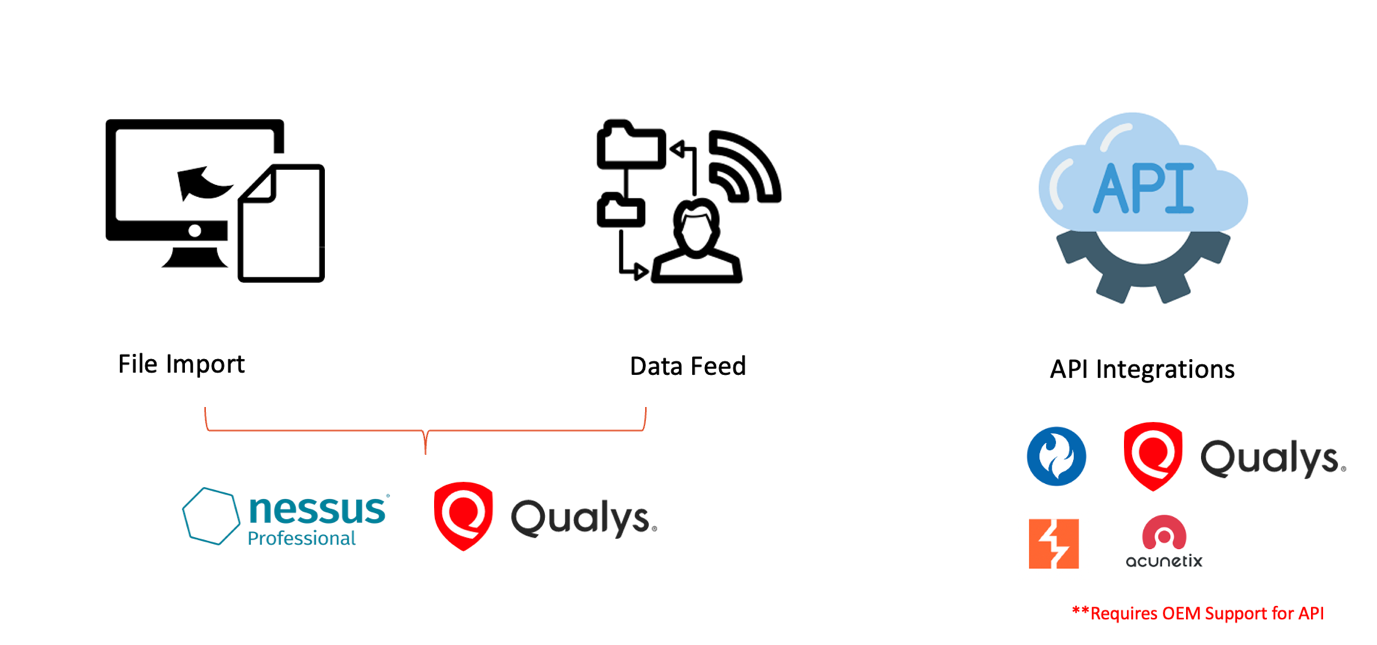
Vulnerability Management
The entire solution is flexible to connect with almost many complex vulnerability management solutions as Qualys, Acunetix , Burpsuite, HCL Appscan and other OEM solutions that provides API. Solution provides 3 modes of integrations Entire platform offers both one way and 2 way integration that provides flexibility to initiate
the entire process from Compliance Foresight and manage the process within the solution itself. It eliminates the process of logging to different tools and fetching reports
• CISO Dashboard , Department Dashboards
• Reduced Overhead in managing Organization Vulnerability
• Single Solution to manage all organization vulnerabilities
• Real Time Dashboards
• Reduced Complexities
• Pre–Defined Reports in excel and PDF
• Trend Analysis of the vulnerabilities across servers, applications and devices
• Business Level Ownerships and Vulnerabilities Closure
• Automatic Patching Compliance
• Tracker for Vulnerability Assessment, Policy Compliance and Web Applications
• Mechanisms to raise exceptions and Exceptions Dashboards
• Track all exceptions and reports and trends on your defined period
• Map Your organization SLA’s and ageing of vulnerability tickets

A Complete Process of the System
VM Process helps the organizations to initiate the scans and manage all data across the infrastructures in a single platform with all scanning process happening at the backend. Once the api’s are integrated, users will just need to manage the scans and all related data across the infrastructures through the common unified platform. It is critical for organization to know the patching status through automated means and not only rely on users to inform the patching pointers. Compliance Foresight – VM Module has a very unique feature where it compares the last 2 scans to suggest if the patching is done. This helps the infra team to verify the patching.
Why Choose us
Whitehats Is the trusted name in Cyber Security and Data Security Consulting with advance automation platform, it makes it easy for customers to trust and deliver the secure business

Bank

Enterprise Customers

MSSP's
CONTACT US
- A - 31, Sector - 4 Noida, UP 201301 India
- sales@whitehats.tech